1.0 Introduction
Suppose you have just taken over as a new system administrator from another person just before they left and they forgot to give you the root password. Now, let's say you have to install the latest version of PHP on the system so that the sales department's website works the way its supposed to. You have to get the website up yesterday, since you are losing money every minute it doesn't work. Or maybe you simply need to add another user to the system.
The above scenarios are just two possible cases when you might need to reset the root password on a system; there are hundreds of other possible cases when you might need to do this, but I am not going to list all of them. Most of us know what to do when something like this happens on a Windows machine, but not a lot of us know how to recover lost passwords from Linux machines. This document attempts to rectify this situation by telling you about the different options available to recover passwords from YOUR machines. (Don't use this to break into other people's systems as that would be stupid and will get you into big trouble if you are caught.)
1.1 Disclaimer
Use the information in this document at your own risk. I disavow any potential liability for the contents of this document. Use of the concepts, examples, and/or other content of this document is entirely at your own risk.
The information in this document should only be used to recover passwords from machines to which you have legal access. If you use this information to break into other people's systems, then I am not responsible for it and you deserve your fate when you are caught. So don't blame me.
You are strongly advised to make a backup of your system before performing any of the actions listed in this document.
1.2 Credits
In this version, I have the pleasure of acknowledging the following people without whose input this would have never seen the light of the day:
- The community at http://www.justlinux.com, for the really helpful debate about this topic in one of their threads.
- The creators and maintainers of the various Linux documentation sites using which I gathered this information.
- Matt Hoskins and Kevin Walsh, for getting me interested in Linux in the first place.
- My friends and family, for bearing with me when I was compiling this document.
1.3 Before you start
Before you attempt to change or replace the password of any machine, make sure you get permission from the management authorizing it, 'cause otherwise it can be mistaken as an attempt to hack into the machine, which is not good.
Secondly, create a backup of all important data before you do anything else, so if anything goes wrong you'll still have a copy of your data. If you didn't, and something went wrong, don't blame me. I tested most of this stuff on my system and it worked, but you are responsible for your system, not me, so don't blame me if something did go wrong.
2.1 Various Options available
There are various methods available for resetting a root password. In this section, I will list all the major ones, and we will go over each in detail later in the document. I will also go over some steps to prevent some other person from doing this and hacking your machine.
The various methods are:
- Boot into single-user mode (easiest, least risky)
- Boot using a boot disk and edit the password file
- Mount the drive on another computer and edit the password file
2.1.1 Reseting passwords by booting into single-user mode
This is the easiest and the fastest method to reset passwords. The steps are a little different depending on if you are using GRUB or LILO as a bootmanager.
Booting into single-user mode from LILO
Follow these steps to reset the password when using LILO:
- Reboot the system. When you see the LILO: prompt (see Fig. 1 below), type in linux singlelinux init=/bin/bash instead. and press 'Enter'. This will log you in as root in single-user mode. If your system requires you to enter your root password to log in, then try
- Once the system finishes booting, you will be logged in as root in single-user mode. Use passwd and choose a new password for root.
- Type reboot to reboot the system and then you can login with the new password you just selected.
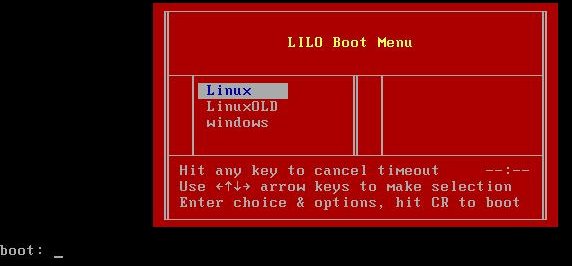
Figure 1. Lilo Boot Menu If you have a new version of LILO which gives you a menu selection of the various kernels available press Tab to get the LILO: prompt and then proceed as shown above.
Booting into single user mode from GRUB
Follow these steps to reset the password when using GRUB:
- Reboot the system, and when you are at the selection prompt (See Fig. 2 below), highlight the line for Linux and press 'e'. You may only have 2 seconds to do this, so be quick.
- This will take you to another screen where you should select the entry that begins with 'kernel' and press 'e' again.
- Append ' single' to the end of that line (without the quotes). Make sure that there is a space between what's there and 'single'. If your system requires you to enter your root password to log into single-user mode, then append init=/bin/bash after 'single'. Hit 'Enter' to save the changes.
- Press 'b' to boot into Single User Mode.
- Once the system finishes booting, you will be logged in as root. Use passwd and choose a new password for root.
- Type reboot to reboot the system, and you can login with the new password you just selected.
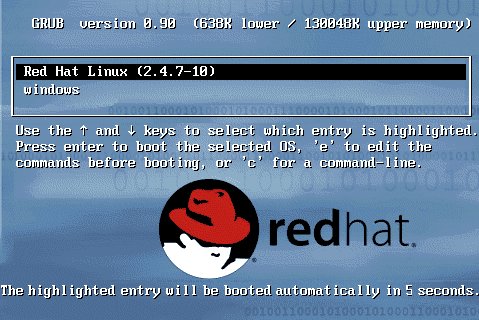
Fig. 2: GRUB Boot Screen 2.1.2 Reseting passwords by using a boot disk and editing the password file
This method is a little bit more complicated than the previous one and has a very high chance of success (assuming your filesystem is not encrypted and you didn't forget the password to decrypt it if it is). As before, get permission before you do this.
To start, you need a Linux boot disk or a rescue disk. (If you didn't create one when prompted during the installation then let this be a lesson for you.) You can use your installation CD as a rescue disk; most distros have an option to allow you to boot into rescue mode. With my Redhat Linux CD, I have to enter linux rescue to start the rescue mode. But this might be a bit different in each distro. You can also use a live linux CD like Knoppix or Gnoppix for system recovery. (Click here for a list of all the live Linux CD's). In this tutorial I will use Knoppix as my rescue CD but the process is almost the same for any rescue CD you might use.
[ You can also download one of the many single-floppy Linux distributions (e.g., Tom's RootBoot ), and use it to bring up the machine as described. This is, of course, much faster than downloading and burning a rescue CD, especially on a slow connection. -- Ben ]
Follow these steps to reset the password using Knoppix:
- Reboot the system and configure it to boot from the Knoppix CD (instructions available here)
- At the Knoppix Boot Prompt (See Fig. 3 below) enter: knoppix lang=us to start boot Knoppix using the english locale. If you understand German, feel free to just hit 'Enter' to boot into Knoppix.
- Once the system finishes booting, press + + (The Control, Alt and F1 key together) to switch to a virtual terminal.
- Type mkdir mountplace to create a directory called 'mountplace'. This is where we will mount the filesystem.
- Type mount /dev/hdaX mountplace, where /dev/hdaX is your root partition. More information on Linux partitions is available here.
- Change to the "/etc" directory on your root partition by typing cd mountplace/etc.
- Use your favorite text editor and open the 'shadow' file for editing. I use 'vi', so I type vi shadow (If you have a really old system, you won't have a shadow file, in which case you need to edit the 'passwd' file.)
- Scroll down to the line containing the root user's information, which looks something like:
root:dsfDSDF!s:12581:0:99999:7::: - Delete everything between the first and second colons, so that the line looks like:
root::12581:0:99999:7::: - Save the file and exit your editor.
- Type cd to return to your home directory.
- Type umount mountplace to unmount the partition.
- Type reboot to reboot your system, and remove the Knoppix CD from the drive.
- Now you can log into your system as root with no password. Make sure you change the password immediately.
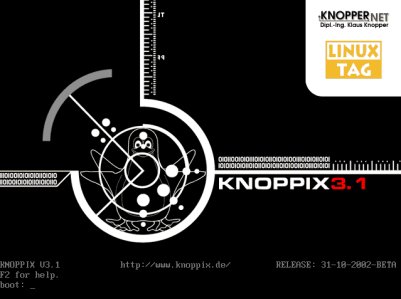
Fig. 3: Knoppix Boot Screen 2.1.2 Reseting passwords by mounting on another system and editing the password file
This option is a bit more work than any of the earlier options but is almost sure to work (except when the filesystem is encrypted).
Follow these steps to reset the password:
- Shut down the machine after backing up all important data.
- Open the casing, unplug the hard drive, and take it to another machine. (This system should be running Linux, since Windows can't read the Linux partition formats.)
- Connect the hard disk as a slave drive and boot the new system.
- Once the system finishes booting, mount the slave drive's root partition as shown above and edit the password file.
3.1 How to Prevent someone else from reseting your root password
If you are an even slightly security-consious sysadmin, the previous sections must have set off alarms while you were reading them. Is it really that easy to hack Linux? Yes and No. It all it comes down to the following: Physical Access is Root Access. Meaning, if you give someone physical access to a system, then you are giving them a very good chance of getting root access on your box. This is true for Windows, Linux, or any other OS out there.
But... you say that you need to give some people physical access to the server? There are some precautions you can take to slow down attackers and stop the noob's. In this section I will talk about various ways you can make your computer more secure against these types of attacks. So lets get started.
3.1.1 Password protecting GRUB and LILO
First, edit the /etc/inittab file and insert the following line, right after the "initdefault" line: ~~:S:wait:/sbin/sulogin. This will require a password to boot into single-user mode by making init run 'sulogin' before dropping the machine to a root shell. 'sulogin' requires the user to input the root password before continuing.
Unfortunately, the above step won't protect us against people who know what they are doing and pass init=/bin/bash to the kernel at the LILO prompt. To prevent unauthorized access I would suggest that you password protect LILO/GRUB by following these steps:
How to Protect LILO:
- Open a shell prompt and log in as root
- Open
/etc/lilo.conf in your favorite text editor - Add the following line before the first image stanza:
password= , where is your password. - Run /sbin/lilo -v to let the changes take effect
- Type chmod 600 /etc/lilo.conf to give only root access to read and edit the file since all passwords are in plain text
- Relax a bit, as your system is a little bit more secure
How to password-protect GRUB
- Open a shell prompt and log in as root
- Type /sbin/grub-md5-crypt and press enter
- Enter the password you chose for GRUB when prompted. This will return an MD5 hash of your password
- Open
/boot/grub/grub.conf in your favorite text editor - Add password --md5 below the timeout in the main section (Replace with the hash you got in the previous step)
- Save and exit
- The next time you reboot, the GRUB menu will not let you access the editor or command interface without first pressing [p] followed by the GRUB password.
3.1.2 Password-protecting the BIOS
There are two primary reasons for password-protecting the BIOS of a computer:
- Prevent Changes To BIOS Settings: if an intruder has access to the BIOS, they can set it to boot off of a diskette or CD-ROM.
- Prevent Booting the System: Some BIOSes allow you to password protect the boot process itself. When activated, an attacker would be forced to enter a password for the BIOS to launch the boot loader.
Because the methods for setting a BIOS password vary between computer manufacturers, you should consult the manual for your computer. If you forget the BIOS password, it can often be reset either with jumpers on the motherboard or by disconnecting the CMOS battery. However, you should check the manual for your computer or motherboard before attempting this procedure.
By Suramya Tomar